If you have an AWS environment and have been using Azure Active Directory(AAD) as your identity store, you would have utilized AWS Single Sign-on to sign in your users into AWS.
With AWS SSO enabled, whenever a user elevates permissions in Azure AD, it can take up to 40 minutes to synchronize permissions to AWS. Though Azure AD offers an option to trigger on-demand provisioning through the Azure portal, unfortunately, it is not supported for AWS SSO. In this blog, I am sharing the steps to trigger on-demand synchronization using Microsoft Graph Explorer:
Pre-requisites
- A user account with Azure global administrator privileges for triggering the on-demand synchronization
- Elevate your permissions to the appropriate AWS role in Azure AD PIM before executing the following steps
Configuration
1. Login into Graph Explorer with a global administrator account
2. GET the App ID for the AWS SSO application by making the following API call:
- Operation — GET
- API Version — beta
- API URL — https://graph.microsoft.com/beta/servicePrincipals?$select=id,appId,displayName&$filter=startswith(displayName,%20%27AWS%20Single%20Sign-on%27)\
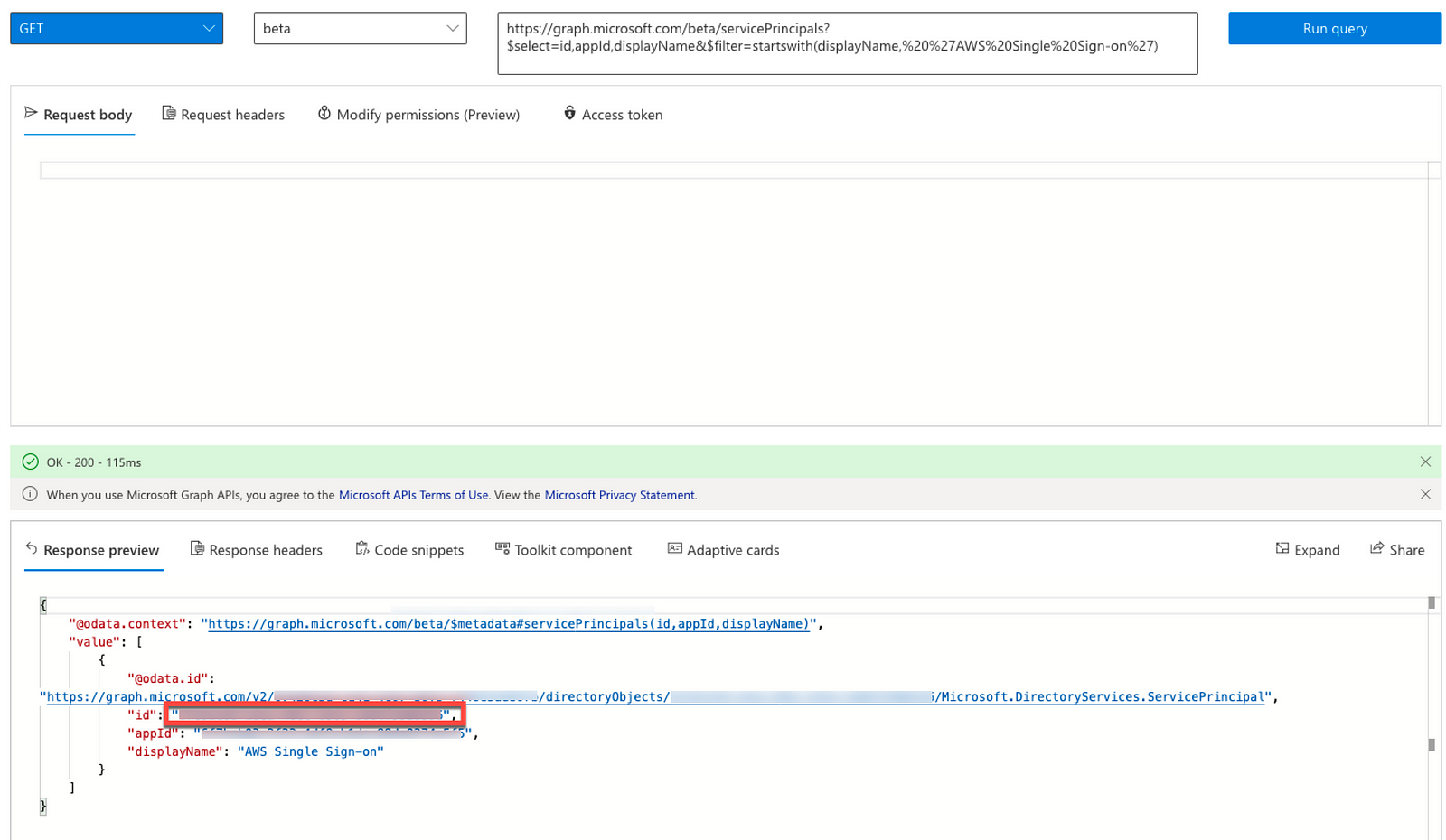
3. Use the ID from the previous step and GET the synchronization jobs by making the following API call:
- Operation — GET
- API Version — beta
- API URL — https://graph.microsoft.com/beta/servicePrincipals/{ID}/synchronization/jobs
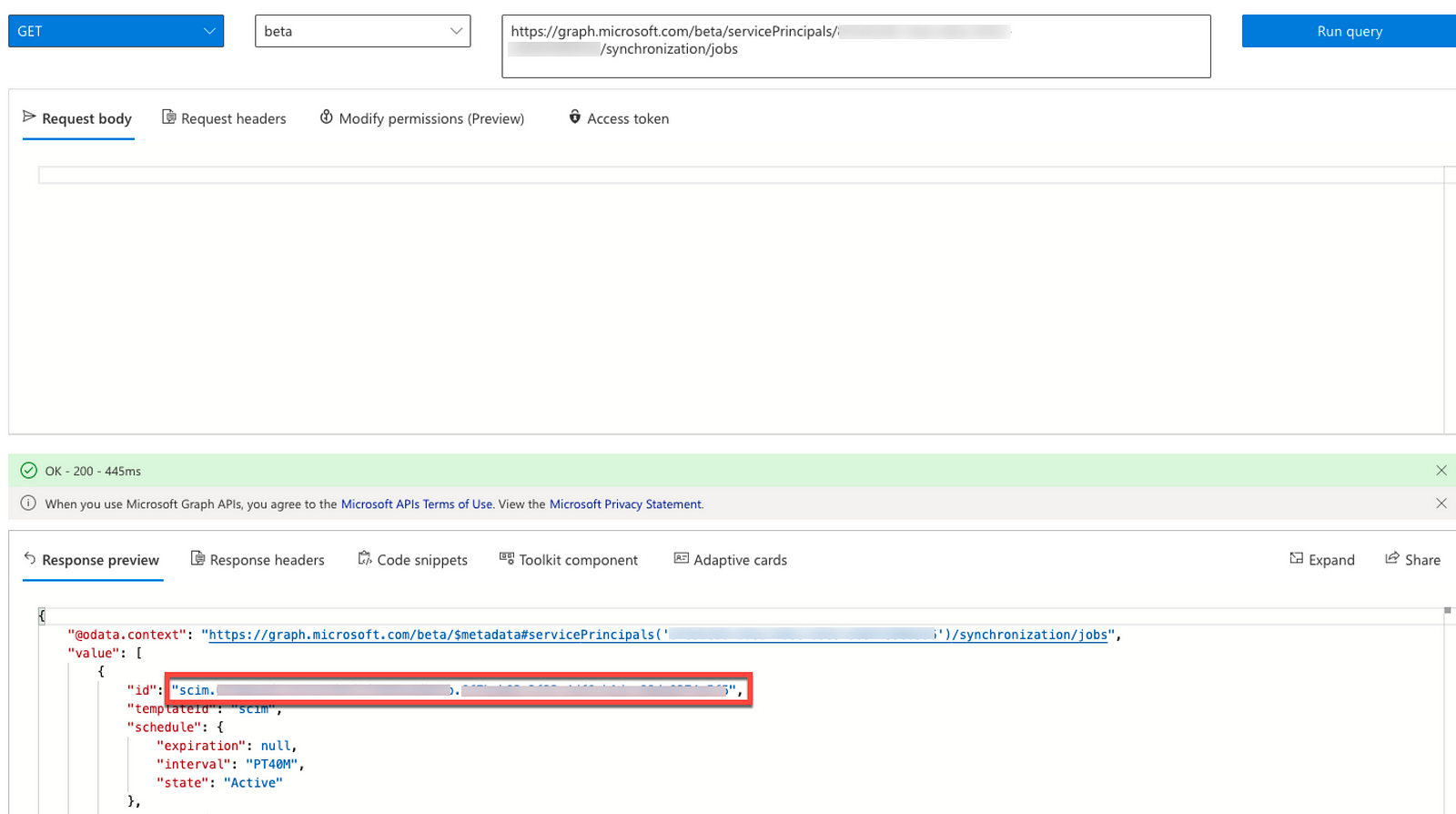
4. Use the service principal id from the second step and synchronization job id from the previous step to trigger the synchronization job on-demand by making the following API call:
- Operation — POST
- API Version — beta
- API URL — https://graph.microsoft.com/beta/servicePrincipals/{ID}/synchronization/jobs/{Job_ID}/start
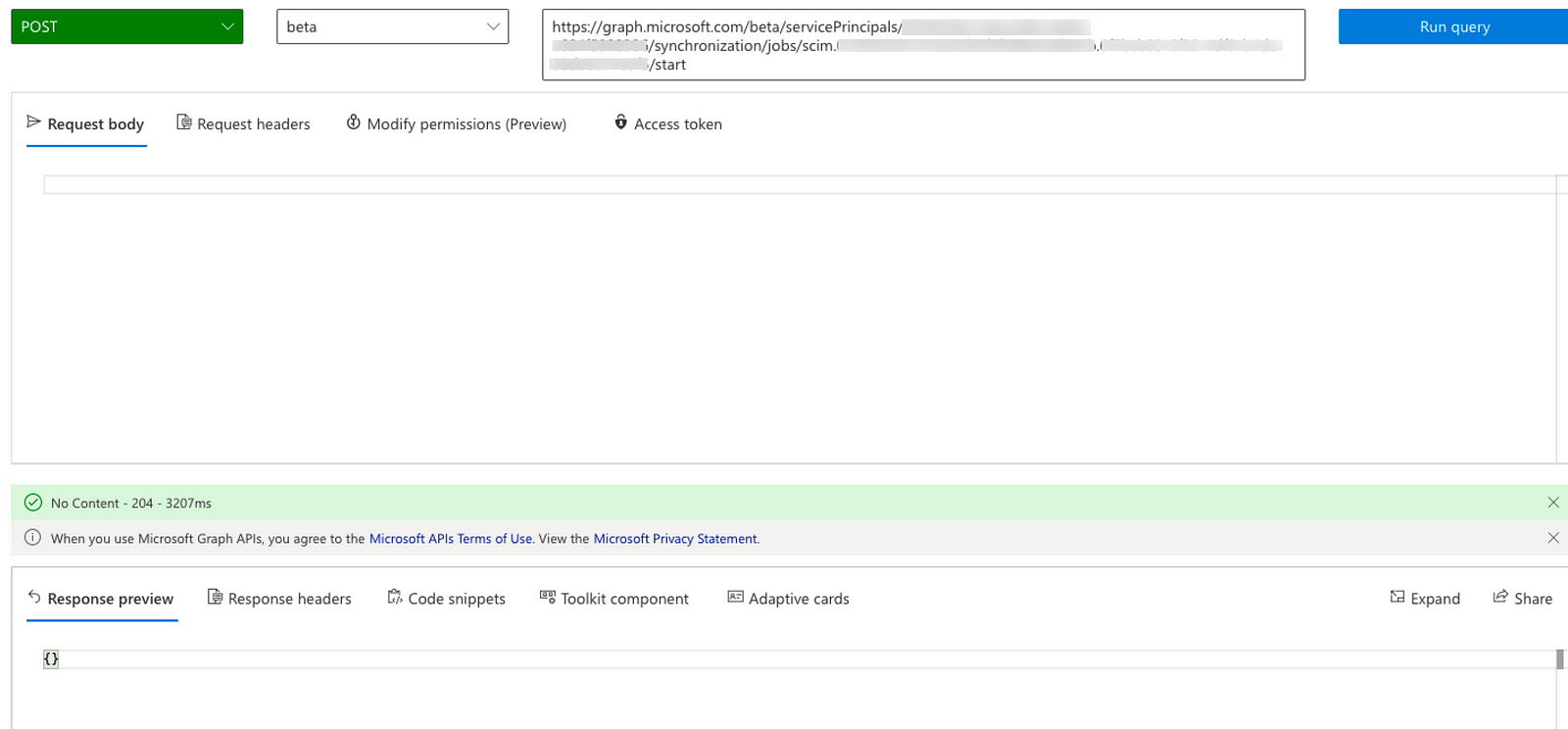
And that’s it. The synchronization will complete within a few seconds, and your users can log in to AWS with updated permissions.